Methodologies for Designing Redundant and Resilient ZeroTRUST Security Architectures using the Mitre Attack Framework
ZeroTrust security architecture is a paradigm shift in network security that assumes that all users, devices, and networks are untrusted by default and that all access to resources must be verified and authenticated before being granted. This approach has become increasingly popular in the wake of the rising number of cyberattacks and data breaches.
In this blog post, we will explore how to use the MITRE ATT&CK framework to design a redundant and resilient ZeroTrust security architecture.
1. Understand the MITRE ATT&CK Framework
The first step in designing a Zero Trust security architecture is to understand the MITRE ATT&CK framework. The MITRE ATT&CK framework is a comprehensive knowledge base of tactics, techniques, and procedures used by attackers. It provides a common language for describing and analyzing cyberattacks, and it helps organizations identify and prioritize potential threats. By understanding the MITRE ATT&CK framework, organizations can develop a better understanding of the types of attacks that they are most likely to face and the vulnerabilities that they need to address.
2. Identify Assets and Threat Actors
The next step is to identify the assets that need to be protected and the types of threat actors that may target them. This includes identifying the data and systems that are most critical to the organization, as well as the types of attackers that are most likely to target them. For example, a healthcare organization may have sensitive patient information that is targeted by nation-state actors, while a financial institution may be targeted by organized crime groups.
3. Conduct a Threat Assessment
Once the assets and threat actors have been identified, the next step is to conduct a threat assessment. This involves using the information gathered in the previous steps to understand the potential risks to the organization and identify vulnerabilities that need to be addressed. The threat assessment should take into account the types of attacks that the organization is most likely to face, as well as the potential impact of a successful attack.
4. Develop a Security Strategy
Based on the results of the threat assessment, the next step is to develop a security strategy that includes both preventive and detective controls. This should include a mix of technical and non-technical controls, such as firewalls, intrusion detection and prevention systems, access controls, and security policies and procedures. The security strategy should also include a plan for incident response, in case an attack is successful.
5. Implement Security Controls
With the security strategy in place, the next step is to implement the security controls identified in the strategy. This may include installing firewalls, intrusion detection and prevention systems, and access controls, as well as implementing security policies and procedures. It's important to ensure that all security controls are configured properly and that they are tested and evaluated regularly to ensure that they are functioning as intended.
6. Continuously Monitor and Update the security architecture
One of the key features of a Zero Trust security architecture is that it is designed to adapt to changing threat landscapes. This means that organizations must continuously monitor for new threats and update their security controls and strategy as needed to stay ahead of emerging threats. This includes regularly reviewing and updating security policies and procedures, as well as testing and evaluating security controls to ensure that they are still effective.
7. Regularly backup important data and systems
Backups and disaster recovery procedures are crucial for resilience. Regularly back-up important data and systems, and have a plan in place for quick disaster recovery and restore operations in the event of an attack.
8. Design for Redundancy and Resilience
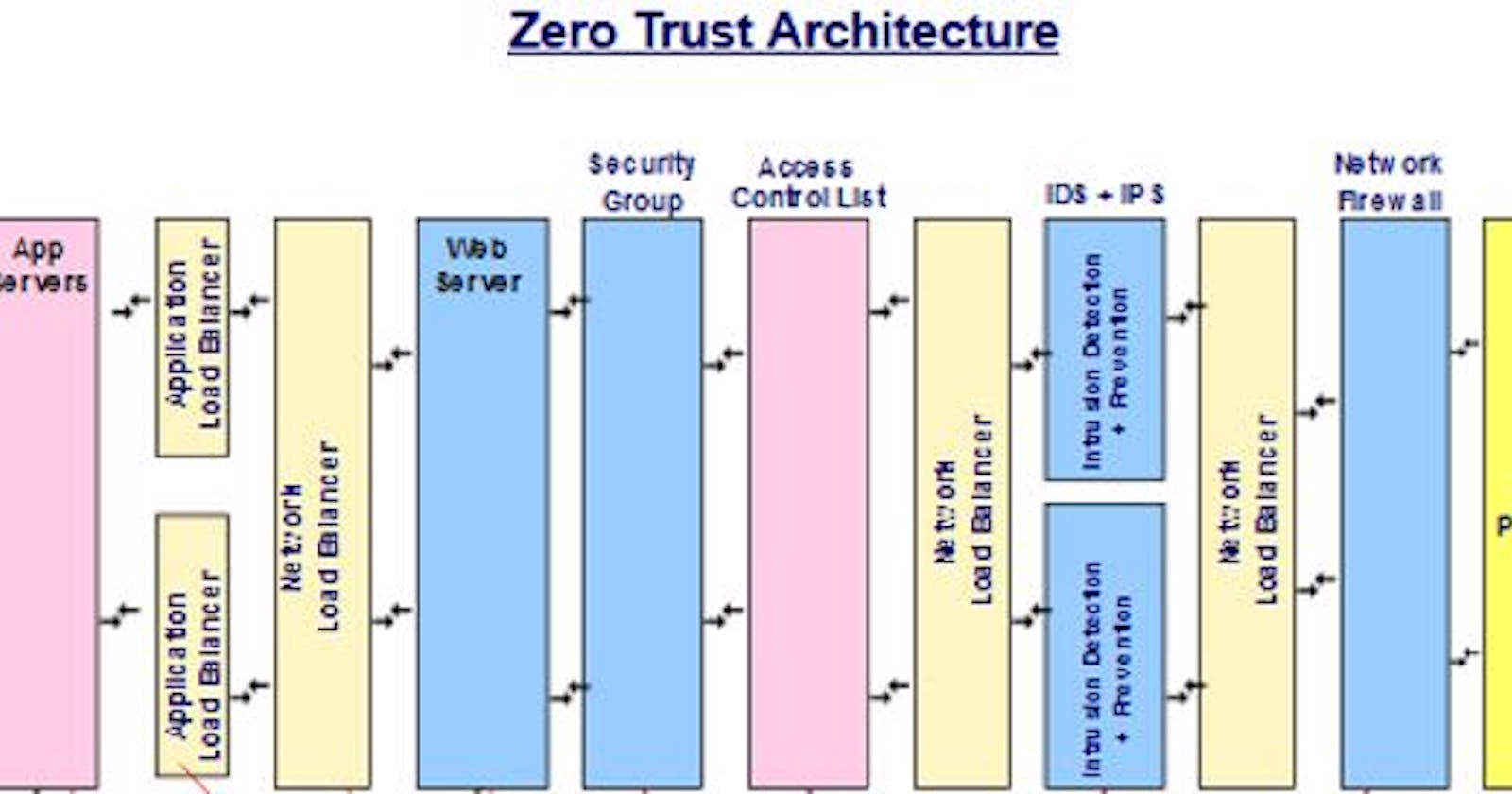
Finally, to design a robust Zero Trust security architecture, organizations should consider implementing redundancy and resilience measures into the design of the architecture. This includes using load balancers, failover mechanisms, and multiple layers of protection to ensure that the system remains available and functional even in the event of an attack or failure.
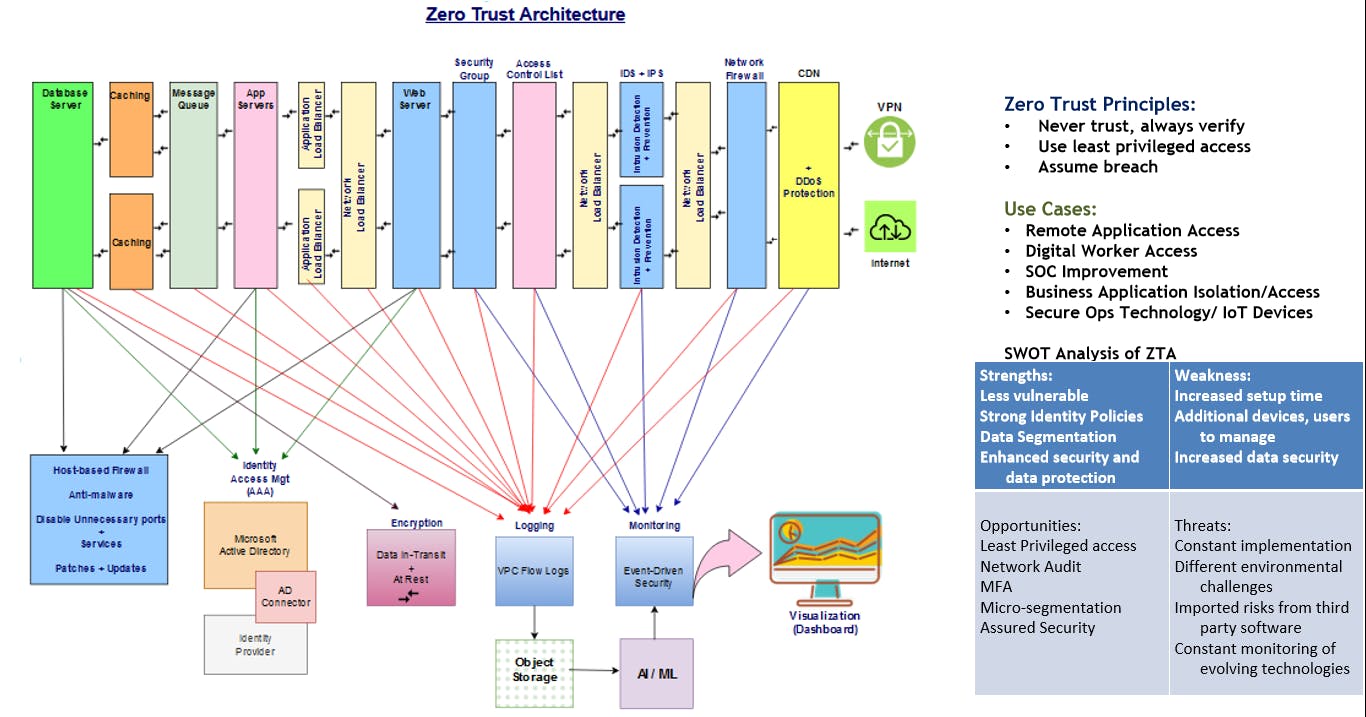
Fig 1: ZeroTrust Security Architecture Overview
Conclusion
The MITRE ATT&CK framework provides a useful tool for organizations looking to design a Zero Trust security architecture. By following these steps, organizations can design security architectures that are both redundant and resilient. This will help protect against the most likely attack vectors and enable the organization to quickly recover from any security incident.